Leaked LockBit 3.0 builder used by ‘Bl00dy’ ransomware gang in attacks
- September 28, 2022
- 03:30 AM ET 12:30 AM PT
- 0

The relatively new Bl00Dy Ransomware Gang has started to use a recently leaked LockBit ransomware builder in attacks against companies.
Last week, the LockBit 3.0 ransomware builder was leaked on Twitter after the LockBit operator had a falling out with his developer. This builder allows anyone to build a fully functional encryptor and decryptor that threat actors can use for attacks.
As the builder includes a configuration file that can easily be customized to use different ransom notes, statistics servers, and features, BleepingComputer predicted that other threat actors would soon use the builder to create their own ransomware.
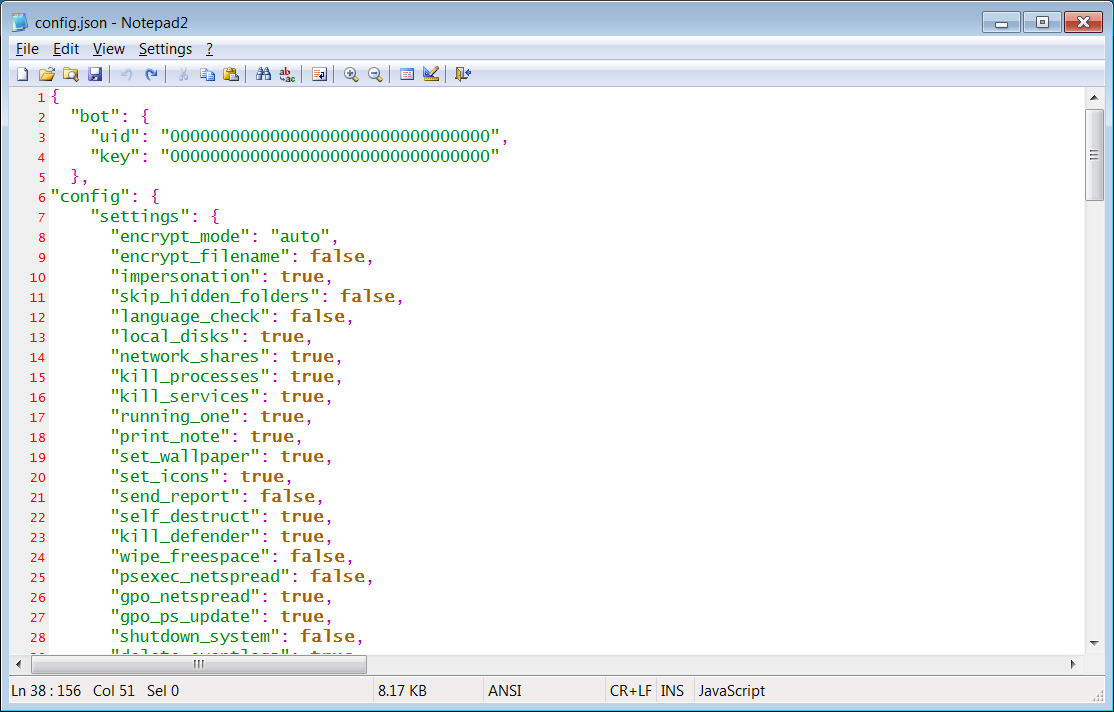
Source: BleepingComputer
Unfortunately, our predictions have come true, and a relatively new ransomware group named 'Bl00Dy Ransomware Gang' has already utilized the builder in an attack on a Ukrainian entity.
The Bl00dy Ransomware Gang
As first reported by DataBreaches.net, the Bl00Dy Ransomware Gang began operating around May 2022, when they targeted a group of medical and dental practices in New York.Like other human-operated ransomware operations, the threat actors breach a network, steal corporate data, and encrypt devices. However, instead of using a Tor data leak site to extort victims and publish stolen data, the threat actors use a Telegram channel for the same purpose.
While this is clearly a 'ransomware' gang, the threat actors do not appear to develop ransomware independently. Instead, they create encryptors using leaked builders and source code of other ransomware operations, such as Babuk [VirusTotal] and Conti [VirusTotal].
On Monday, cybersecurity researcher Vladislav Radetskiy released a report on a new Bl00Dy Ransomware Gang encryptor that was found in an attack on a Ukrainian victim.
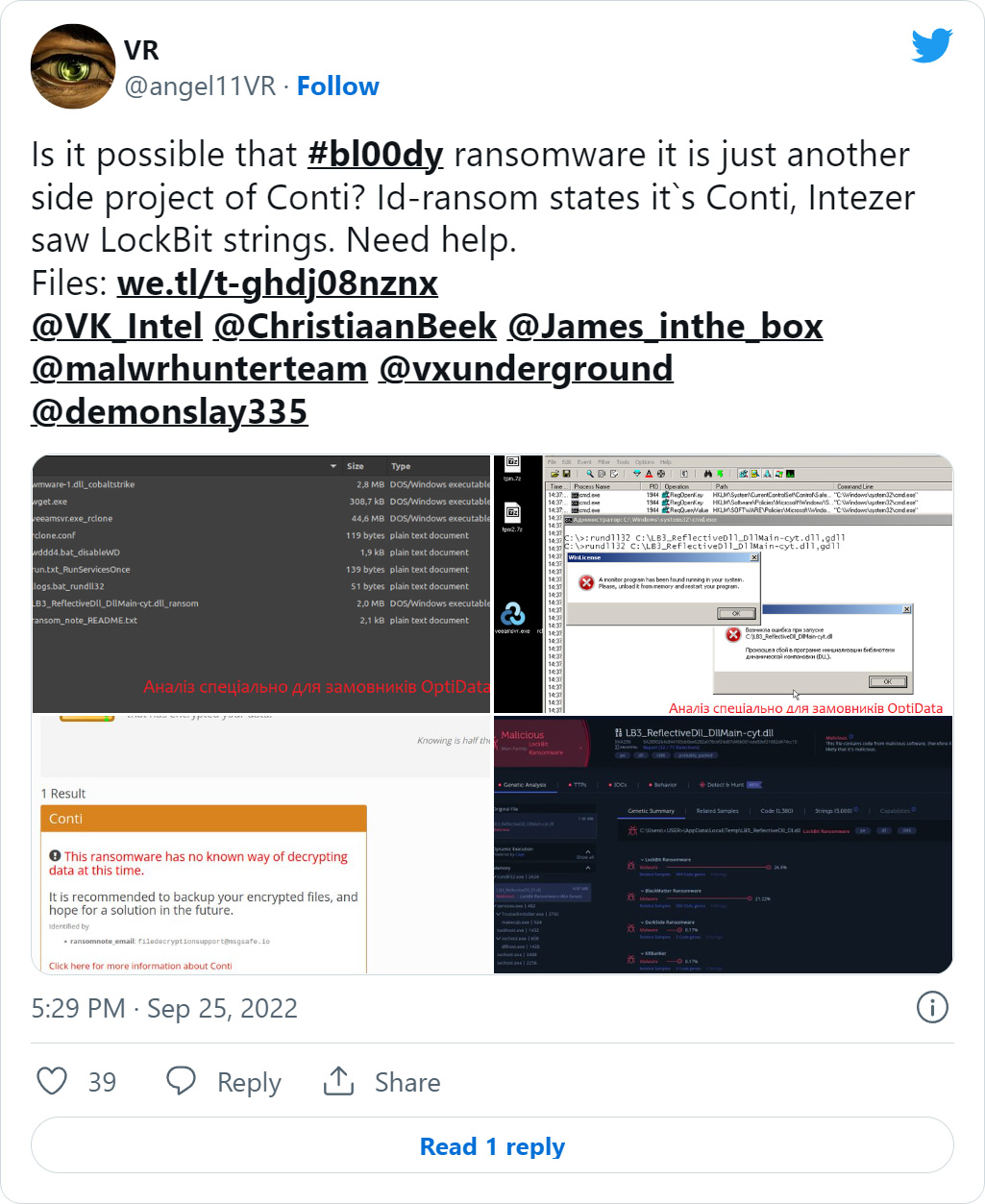
However, it was unclear if the ransomware was based on Conti or LockBit, as the '[email protected]' email was previously in an encryptor built from the leaked Conti source code.
Researcher MalwareHunterTeam later confirmed that the encryptor was built using the recently released LockBit 3.0 builder. An Intezer scan also showed a lot of code overlap between the Bl00dy and LockBit 3.0 encryptors.
BleepingComputer gave the Bl00dy Ransomware Gang's encrypter a test and found some differences between this new encryptor and previous ones.
In past campaigns, the threat actors added the .bl00dy extension for encrypted files. However, as this is not a customizable option in the LockBit 3.0 builder, the threat actors are left using extensions determined when the encryptor is built.
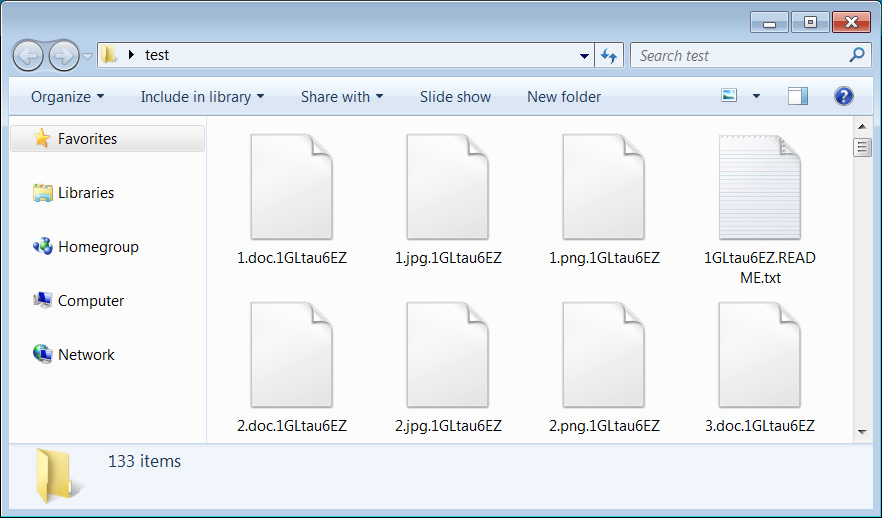
Source: BleepingComputer
As for the ransom note, the file names are still created in LockBit-style, but the threat actors have customized them to include their own text and contact information, as shown below.
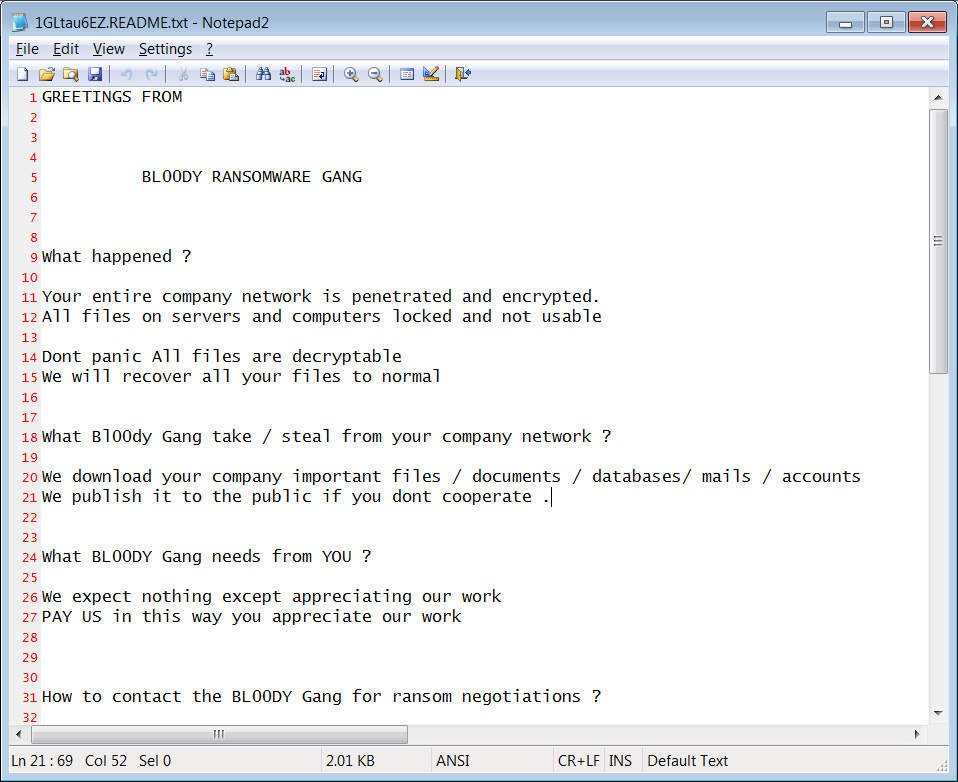
Source: BleepingComputer
Ultimately, though, this is a LockBit 3.0 ransomware encryptor, so it supports all of the features previously reported by security researchers.
It would not be surprising to see the Bl00dy Ransomware Gang switch between ransomware families as needed to either evade detection or take advantage of various features.
The LockBit operation launched in September 2019 and has since grown into one of the most active, feature-rich Ransomware-as-a-Service operations at this time.
LockBit 3.0 was released in June 2022 with new extortion tactics, a redesigned encryptor using code from BlackMatter, and the first ransomware bug bounty program.
As the leaked LockBit 3.0 ransomware builder is easily customizable by other threat actors, we will see other threat actors soon using it in their own attacks.