- Joined
- Jun 26, 2021
- Messages
- 987
Chinese hackers use Google Drive to drop malware on govt networks
- November 18, 2022
- 10:24 AM
- 0

State-backed Chinese hackers launched a spearphishing campaign to deliver custom malware stored in Google Drive to government, research, and academic organizations worldwide.
The attacks have been observed between March and October 2022 and researchers attributed it to the cyber espionage group Mustang Panda (Bronze President, TA416).
According to Trend Micro researchers, the threat group targeted mostly organizations in Australia, Japan, Taiwan, Myanmar, and the Philippines.
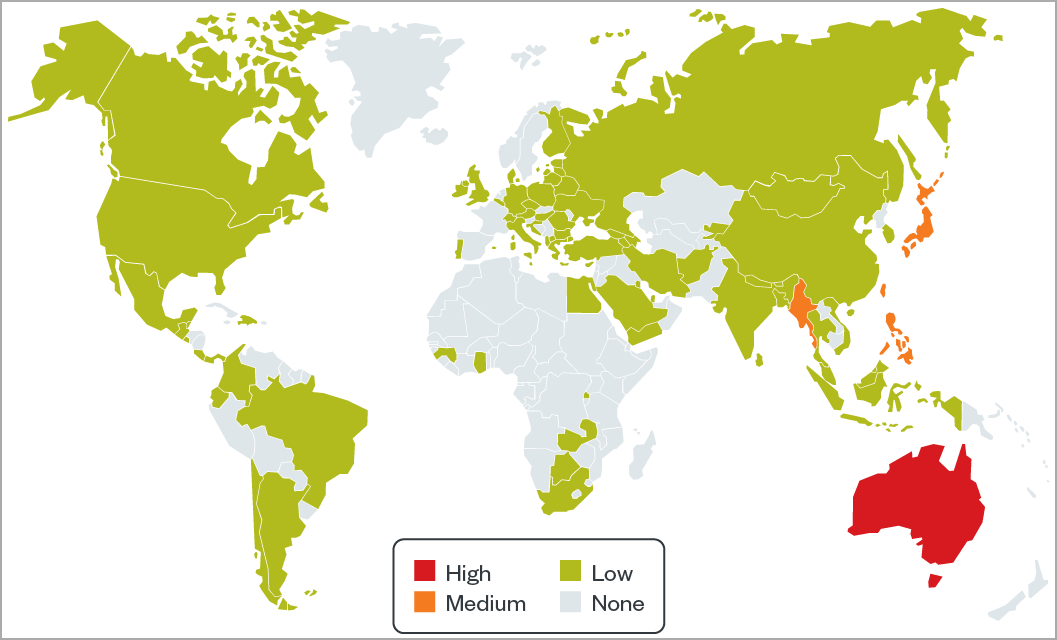
The Chinese hackers used Google accounts to send their targets email messages with lures that tricked them into downloading custom malware from Google Drive links.
Infection details
In a report today, Trend Micro researchers say that the hackers used messages with geopolitical subjects and that most of them (84%) targeted government/legal organizations.To bypass security mechanisms, the embedded link points to a Google Drive or Dropbox folder, both legitimate platforms with good reputation that are typically less suspicious.
These links lead to downloading compressed files (RAR, ZIP, JAR) with custom malware strains such as ToneShell, ToneIns, and PubLoad.
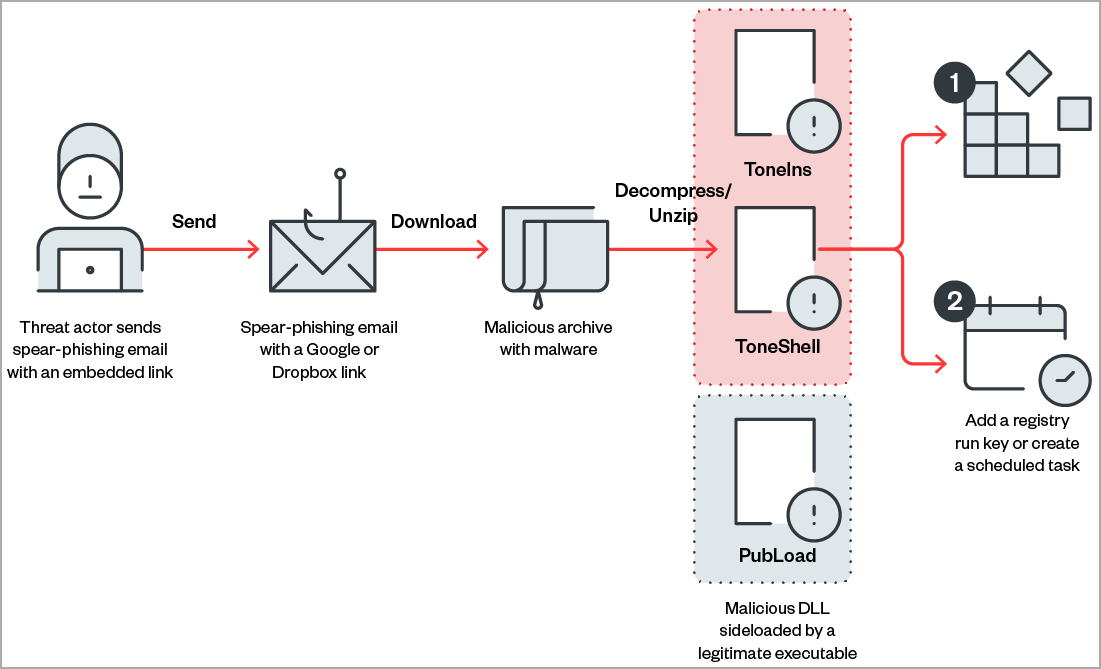
"The email's subject might be empty or might have the same name as the malicious archive," explains the report.
"Rather than add the victims' addresses to the email's "To" header, the threat actors used fake emails. Meanwhile, the real victims' addresses were written in the "CC" header, likely to evade security analysis and slow down investigations." - Trend Micro
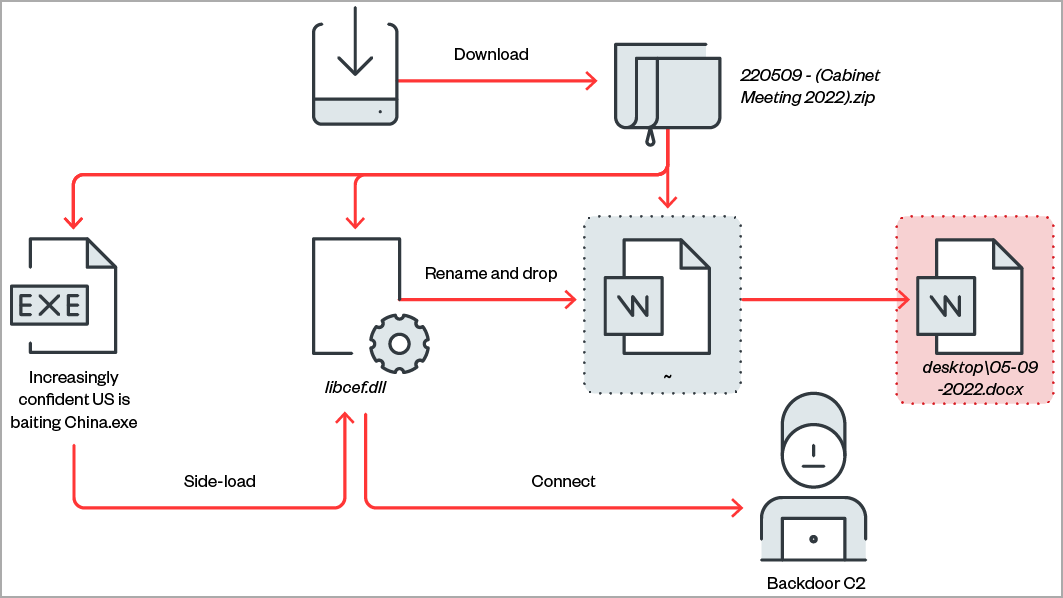
Although the hackers used various malware loading routines, the process typically involved DLL side-loading after the victim launched an executable present in the archives. A decoy document is displayed in the foreground to minimize suspicions.
Malware evolution
The three malware strains used in this campaign are PubLoad, ToneIns, and ToneShell.From the three custom malware pieces used in the campaign, only PubLoad has been previously documented in a Cisco Talos report from May 2022 describing campaigns against European targets.
PubLoad is a stager responsible for creating persistence by adding registry keys and creating scheduled tasks, decrypting shellcode, and handling command and control (C2) communications.
Trend Micro says later versions of PubLoad feature more sophisticated anti-analysis mechanisms, implying that Mustang Panda is actively working on improving the tool.
ToneIns is an installer for ToneShell, the main backdoor used in the recent campaign. It uses obfuscation to evade detection and load ToneShell while also establishing persistence on the compromised system.
ToneShell is a standalone backdoor loaded directly in memory, featuring code flow obfuscation through implementation of custom exception handlers.
This also works as an anti-sandbox mechanism, as the backdoor won't execute in a debugging environment.
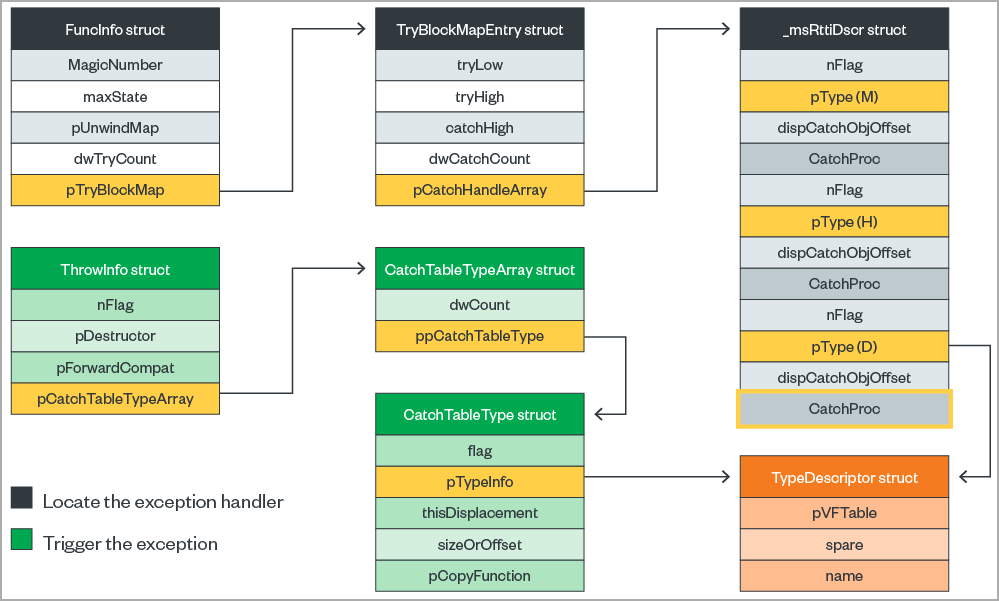
source: Trend Micro
After connecting to the C2, ToneShell sends a package with victim ID data and then waits for new instructions.
These commands allow uploading, downloading, and executing files, creating shells for intranet data exchange, changing sleep configuration, and more.
Mustang Panda activity
Trend Micro says this recent campaign features the same Mustang Panda techniques, tactics, and procedures (TTPs) that Secureworks reported in September 2022.The latest campaign shows signs of an improved toolset and capability to expand, which increases the Chinese hackers' ability to collect intelligence and breach targets.
Earlier this year, Proofpoint reported that Mustang Panda was focusing its operations in Europe, targeting high-ranking diplomats.
A Secureworks report from around the same time spotted a separate Mustang Panda campaign, this time targeting on Russian officials.
In March 2022, ESET explored Mustang Panda's operations in Southeast Asia, South Europe, and Africa, indicating that the Chinese espionage gang is a global threat despite having short-term bursts of focused activity.