- Joined
- Jun 26, 2021
- Messages
- 1,005
- September 13, 2023 ET
- 02:27 PM
- 0

Microsoft added a new security feature to Windows 11 that lets admins block NTLM over SMB to prevent pass-the-hash, NTLM relay, or password-cracking attacks.
This will modify the legacy approach where Kerberos and NTLM (i.e., LM, NTLM, and NTLMv2) authentication negotiations with destination servers would be powered by Windows SPNEGO.
When connecting to a remote SMB share, Windows will try to negotiate authentication with the remote computer by performing an NTLM challenge response.
However, this NTLM challenge response will contain the hashed password of the logged-in user trying to open the SMB share, which can then be captured by the server hosting the share.
These hashes can then be cracked to retrieve the plaintext password or used in NTLM Relay and pass-the-hash attacks to log in as the user.
This new feature allows an admin to block outbound NTLM over SMB, preventing a user's hashed password from being sent to a remote server, effectively preventing these types of attacks.
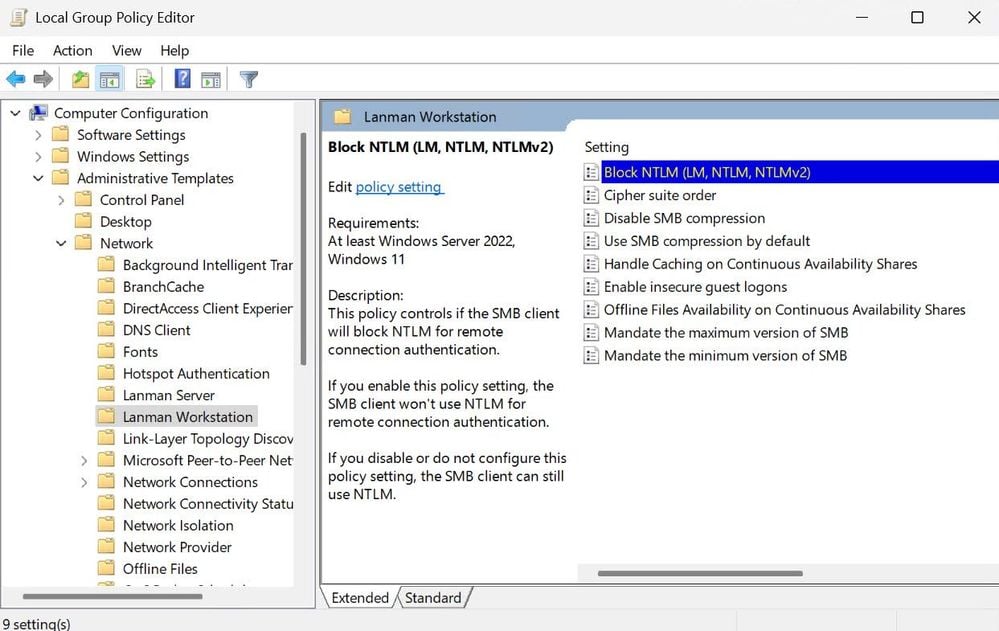
"With this new option, an administrator can intentionally block Windows from offering NTLM via SMB," Microsoft's Amanda Langowski and Brandon LeBlanc explained.
"An attacker who tricks a user or application into sending NTLM challenge responses to a malicious server will no longer receive any NTLM data and cannot brute force, crack, or pass a password, as they will never be sent over the network."
This additional security layer eliminates the need to completely shut down NTLM usage within the operating system.
Starting with Windows 11 Insider Preview Build 25951, admins can configure Windows to block sending NTLM data over SMB on remote outbound connections using Group Policy and PowerShell.
They can also entirely turn off NTLM usage in SMB connections using NET USE and PowerShell.
Another new option available starting this build is SMB dialect management, which allows admins to block older and insecure Windows devices from connecting by toggling off the use of older SMB protocols within their organization."
"A later Windows Insider release will allow administrators to control SMB NTLM blocking to specific servers with an allow list," added Ned Pyle, Principal Program Manager in the Windows Server engineering group, in a separate blog post.
"A client will be able to specify SMB servers that only support NTLM - either as non-domain members or third-party products - and allow connection."
SMB signing requirement to block attacks
With the release of Windows 11 Insider Preview Build 25381 to the Canary Channel, Redmond also started requiring SMB signing (aka security signatures) by default for all connections to defend against NTLM relay attacks.In these attacks, malicious actors force network devices, including domain controllers, to authenticate against servers under their control to take complete control over the Windows domain by impersonating them.
SMB signing is an SMB security mechanism that plays a crucial role in thwarting malicious authentication requests by verifying the sender and receiver's identities through the use of embedded signatures and hashes appended to each message.
It has been available starting with Windows 98 and 2000, and it has been updated in Windows 11 and Windows Server 2022 to improve protection and performance by significantly accelerating data encryption speeds.
These updates are part of a broader initiative to enhance the security of Windows and Windows Server, as highlighted by previous announcements made throughout 2022.
In April 2022, Microsoft took a significant step when it announced the final phase of disabling the three-decade-old SMB1 file-sharing protocol in Windows for Windows 11 Home Insiders.
Continuing this trajectory, the company unveiled enhanced defense measures against brute-force attacks five months later, introducing an SMB authentication rate limiter designed to mitigate the impact of unsuccessful inbound NTLM authentication endeavors.