Ransomware data theft tool may show a shift in extortion tactics
- September 25, 2022
- 11:14 AM ET
- 0

Data exfiltration malware known as Exmatter and previously linked with the BlackMatter ransomware group is now being upgraded with data corruption functionality that may indicate a new tactic that ransomware affiliates might switch to in the future.
The new sample was spotted by malware analysts with the Cyderes Special Operations team during a recent incident response following a BlackCat ransomware attack and later shared with the Stairwell Threat Research team for further analysis (Symantec saw a similar sample deployed in a Noberus ransomware attack).
While Exmatter has been used by BlackMatter affiliates since at least October 2021, this is the first time the malicious tool was seen sporting a destructive module.
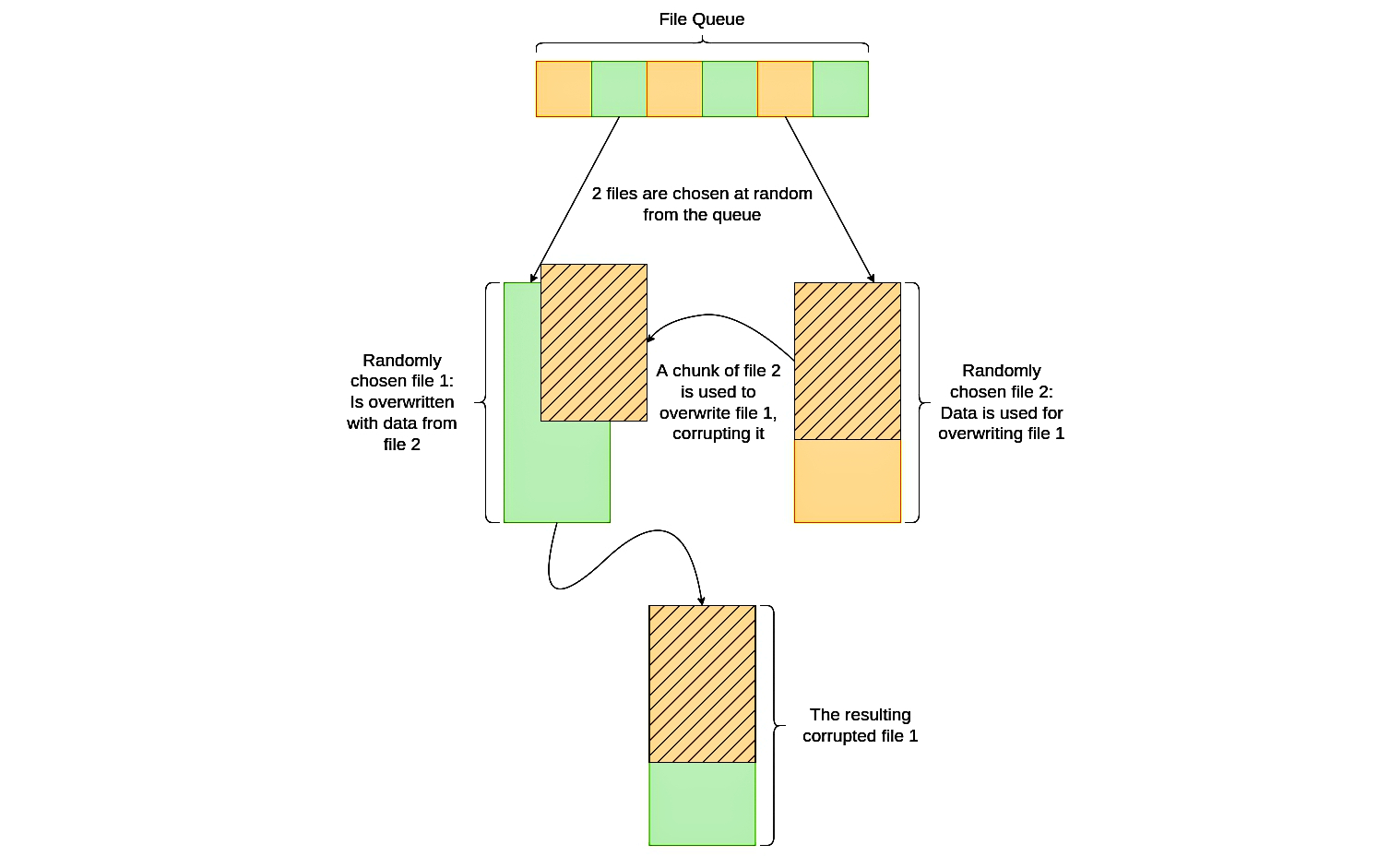
"As files upload to the actor-controlled server, the files that have been successfully copied to the remote server are queued to be processed by a class named Eraser," Cyderes said.
"A randomly sized segment starting at the beginning of the second file is read into a buffer and then written into the beginning of the first file, overwriting it and corrupting the file."
This tactic of using data from one exfiltrated file to corrupt another file might be part of an attempt to evade ransomware or wiper heuristic-based detection that could trigger when using randomly generated data.
As Stairwell threat researchers found, Exmatter's partially-implemented data destruction capabilities are likely still in development given that:
- There is no mechanism for removing files from the corruption queue, meaning that some files may be overwritten numerous times before the program terminates, while others may never have been selected.
- The function that instantiates the Eraser class, named Erase, does not appear to be fully implemented and does not decompile correctly.
The second file’s chunk length, which is used to overwrite the first file, is randomly decided and could be as short as one byte long.
Switch to data corruption to keep all the money?
This data corruption feature is an interesting development, and while it may also be used to evade security software, researchers at Stairwell and Cyderes think it may be part of a shift in the strategy used by ransomware affiliates.Many ransomware operations run as a Ransomware-as-a-Service, where operators/developers are in charge of developing the ransomware, payment site, and handling negotiations, while affiliates join to breach corporate networks, steal data, delete backups, and encrypt devices.
As part of this arrangement, the ransomware operators receive between 15-30% of any ransom payment, and the affiliates receive the rest.
However, ransomware operations have been known in the past to introduce bugs that have allowed security researchers to create decryptors that help victims recover files for free.
When this happens, the affiliates lose out on any potential revenue they would have received as part of a ransom payment.
Due to this, the researchers believe that this new data corruption feature could be a new shift from traditional ransomware attacks, where data is stolen and then encrypted, to attacks where data is stolen and then deleted or corrupted.
Under this method, the affiliate gets to keep all of the revenue generated from an attack, as they don't need to share a percentage with the encryptor developer.
"Affiliates have also lost out on profits from successful intrusions due to exploitable flaws in the ransomware deployed, as was the case with BlackMatter, the ransomware associated with previous appearances of this .NET-based exfiltration tool," Cyders added.
Destroying the sensitive data after exfiltrating it to their servers will prevent this from happening and will most likely also act as an additional incentive for victims to pay the ransom demands.
"Eliminating the step of encrypting the data makes the process faster and eliminates the risk of not getting the full payout, or that the victim will find other ways to decrypt the data," Cyders said.
This might be why we're seeing exfiltration tools in the process of being upgraded with in-development data corruption capabilities that would likely allow RaaS affiliates to remove the ransomware deployment part in their attacks to keep all the money for themselves.
"Additionally, for each extorted payment received, the operator would retain 100% of the ransom payment, as opposed to paying a percentage to the RaaS developers," concluded Stairwell threat researcher Daniel Mayer.
"These factors culminate in a justifiable case for affiliates leaving the RaaS model to strike it out on their own, replacing development-heavy ransomware with data destruction."